Telecommunications Systems: Principles and Implementing Voice, Data, and Video Communication Solutions

In today’s interconnected world, telecommunications systems play a crucial role in facilitating communication and collaboration between individuals and businesses. These systems encompass voice, data, and video communication solutions, enabling seamless communication over various channels. In this article, we will explore the principles of telecommunications systems and discuss the implementation of voice, data, and video communication […]
Designing and Managing Wireless Networks with Digital Systems Integration, Inc.

In the modern business landscape, wireless networks have become an indispensable part of communication and connectivity. They offer unparalleled flexibility, mobility, and convenience for employees, customers, and partners. However, designing, deploying, and managing wireless networks can be a challenging task. This article delves into the world of wireless networks and how Digital Systems Integration, Inc. […]
Low-Voltage Contractors in Brevard County and Surrounding Areas: Enhancing Your Business with Structured Cabling Solutions

In today’s fast-paced business environment, reliable and efficient communication systems are essential for success. Low-voltage contractors play a crucial role in designing, installing, and maintaining these systems, ensuring seamless connectivity and optimal performance. This article explores how structured cabling solutions provided by experienced low-voltage contractors can benefit businesses in Brevard County, including cities and towns […]
Digital Systems Integration, Inc: Structured Cabling and Network Solutions

Introduction to Digital Systems Integration, Inc Digital Systems Integration, Inc (DSI) is a leading provider of structured cabling and network infrastructure solutions. With their vast experience in the industry, DSI offers a wide range of services tailored to meet the diverse needs of businesses. In this article, we will discuss the various services provided by […]
DSI Partners with CyberHoot
Reposted from CyberHoot CyberHoot is excited to announce our newest partnership with DSI, a leading Managed Service Provider (MSP) committed to delivering security awareness and testing solutions to businesses they support. This partnership enables DSI to provide their clients with a leading cybersecurity awareness training and innovative Phish Testing solution. “Thanks to CyberHoot, we were […]
Structured Cabling Solutions for West Melbourne, Florida Businesses
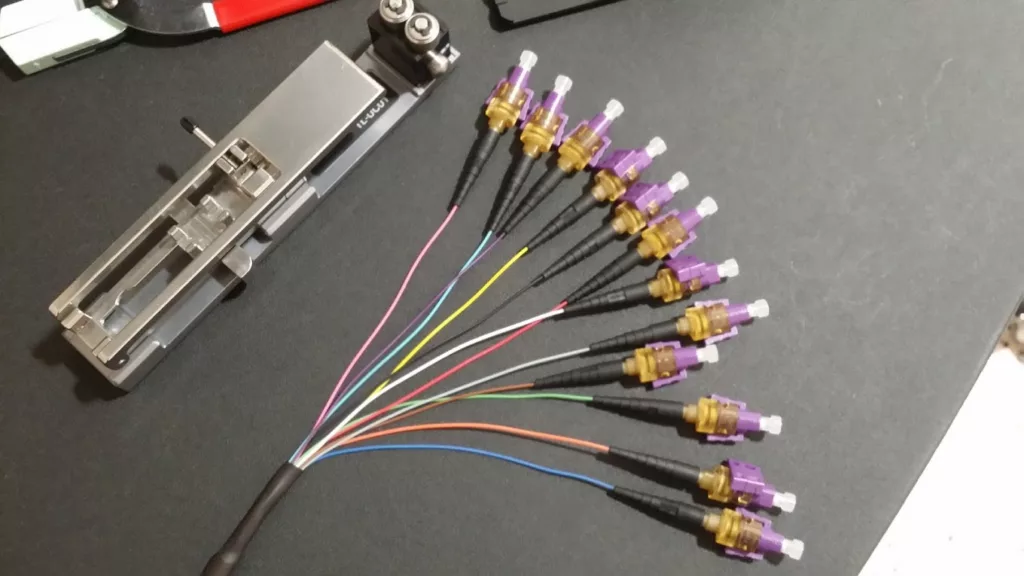
In the digital age, a reliable, high-performance network infrastructure is crucial for businesses to stay competitive and efficient. Structured cabling plays a vital role in ensuring seamless connectivity, enabling businesses to achieve optimal performance and productivity. At Digital Solutions, Inc. (DSI), we specialize in providing top-notch structured cabling and point-to-point cabling services for businesses in […]
Revolutionize Your Business Communications with VoIP Solutions in Melbourne, Florida
In the modern business world, effective communication is crucial for success. Voice over Internet Protocol (VoIP) technology has revolutionized the way businesses communicate by offering increased flexibility, functionality, and cost savings compared to traditional telephony systems. At Digital Solutions, Inc. (DSI), we specialize in providing comprehensive VoIP solutions for businesses in Melbourne, Florida, Brevard County, […]
Structured Cabling Solutions in Melbourne, Florida

Comprehensive and Customized Services for Your Business In today’s fast-paced business environment, having a robust and reliable network infrastructure is essential. As businesses continue to rely on technology for their daily operations, the need for structured cabling solutions has become more critical than ever. At DSI (Digital Solutions, Inc.), we specialize in providing comprehensive and […]
Business Copier and Printer Service in Melbourne, Florida

Get the Best Managed Printing Solutions Are you searching for reliable and professional business copier and printer service in Melbourne, Florida? Look no further! We, at DSI (Digital Solutions, Inc.), offer top-notch managed printing solutions for businesses in Brevard and adjacent counties. Our goal is to provide our customers with the best printer repair, maintenance, […]
Update Debian-Based Linux Machines
Keep your Debian-based Linux system up-to-date by following these simple steps to update packages and the system itself using the command line. Step 1: Open the Terminal Access the terminal with Ctrl + Alt + T or search for “Terminal” or “Konsole” in your system’s application menu. Step 2: Update Package List, Upgrade Installed Packages, […]

