As cyber threats continue to evolve, the need for robust cybersecurity measures has never been more critical. The Cybersecurity Maturity Model Certification (CMMC) and the NIST SP 800-171 are frameworks designed to enhance the protection of sensitive information and improve cybersecurity practices across industries. In this article, we’ll outline the first ten steps your organization can take towards achieving CMMC and NIST 800-171 compliance.
1. Understand the Requirements
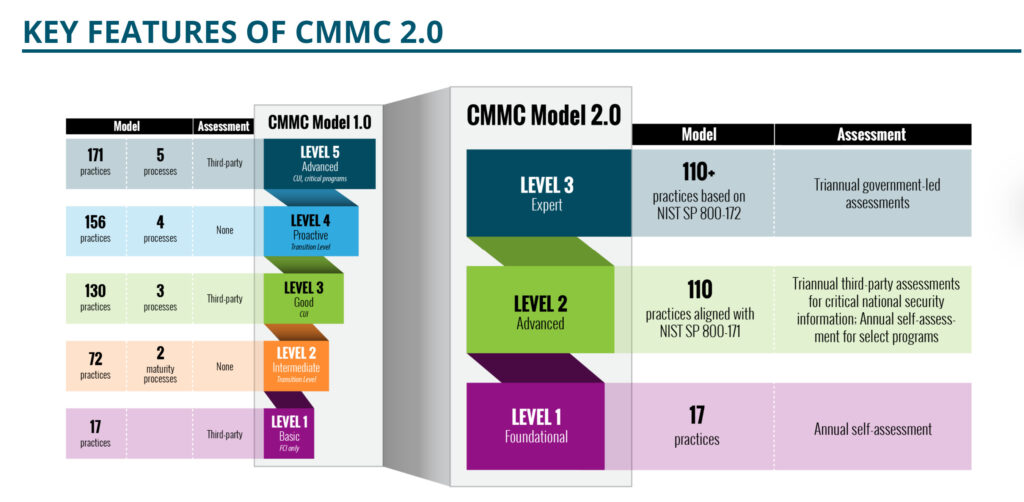
The first step towards compliance is understanding the requirements of both the CMMC and NIST 800-171 frameworks. Familiarize yourself with the various levels of CMMC, ranging from Level 1 (basic cybersecurity) to Level 5 (advanced cybersecurity), and identify the specific requirements that apply to your organization.
2. Identify and Categorize Sensitive Information
Identify and categorize all sensitive information within your organization, including Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). Determine which systems, networks, and devices store, process, or transmit this sensitive data.
3. Conduct a Gap Analysis
Perform a gap analysis to evaluate your organization’s current cybersecurity posture against the requirements of the CMMC and NIST 800-171. This analysis will help you identify areas of non-compliance and prioritize the necessary actions to address these gaps.
4. Develop a System Security Plan (SSP)
Create a System Security Plan (SSP) that outlines your organization’s current security measures, as well as any planned improvements. The SSP should provide a detailed description of your system’s environment, including hardware, software, and network components.
5. Implement Required Security Controls
Begin implementing the required security controls based on the results of your gap analysis. This may include updating policies and procedures, strengthening access controls, implementing multi-factor authentication, and enhancing incident response capabilities.
6. Train and Educate Your Workforce
Provide ongoing cybersecurity training and education for your employees to ensure they understand their roles and responsibilities in maintaining a secure environment. This includes training on security awareness, phishing prevention, and proper handling of sensitive information.
7. Monitor and Maintain Your Security Posture
Regularly monitor your systems and networks to detect potential threats and vulnerabilities. This includes implementing continuous monitoring tools, conducting vulnerability assessments, and performing regular audits of your security controls.
8. Develop an Incident Response Plan
Create a comprehensive incident response plan that outlines the steps your organization will take in the event of a security incident. This plan should include roles and responsibilities, communication protocols, and procedures for containment, eradication, and recovery.
9. Establish a Continuous Improvement Process
Implement a continuous improvement process to ensure your organization’s security posture evolves as new threats and vulnerabilities emerge. Regularly review and update your security policies, procedures, and controls, and make adjustments based on lessons learned from incidents and industry best practices.
10. Seek Professional Guidance
Consider engaging with a qualified third-party consultant or managed security services provider to assist with your CMMC and NIST 800-171 compliance efforts. These experts can provide valuable guidance, recommendations, and support throughout the compliance process.
By taking these initial steps towards CMMC and NIST 800-171 compliance, your organization will be well on its way to establishing a strong cybersecurity foundation. Implementing these frameworks will not only protect your sensitive information but also enhance your overall security posture and resilience against cyber threats.

